Difference between revisions of "Mesh/Flashing extender nodes"
| (9 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
After following the [Mesh/WalkThrough], you are probably just an isolated node on the virtual People's Open Network. If you want to become part of the physical mesh, you are going to need to extend the signal from home node using what we call an extender node. An extender node is just a roof-mounted, directional antenna used to make point-to-point connections between two locations that have line-of-sight (LOS) to one another. Preparing an extender node generally consists to two stages, downgrading the proprietary AirOS firmware and flashing it with our custom build of OpenWrt. | After following the [[Mesh/WalkThrough]], you are probably just an isolated node on the virtual People's Open Network. If you want to become part of the physical mesh, you are going to need to extend the signal from home node using what we call an extender node. An extender node is just a roof-mounted, directional antenna used to make point-to-point connections between two locations that have line-of-sight (LOS) to one another. Preparing an extender node generally consists to two stages, downgrading the proprietary AirOS firmware and flashing it with our custom build of OpenWrt. | ||
== Downgrading to | == Downgrading to older AirOS == | ||
Typically, we use Ubiquiti equipment for our extender nodes. These come with a proprietary firmware called AirOS. Any extender node with version 5.6 of AirOS and above needs to be downgraded to a 5.5.XX version of AirOS version before you can flash it with OpenWRT. | Typically, we use Ubiquiti equipment for our extender nodes. These come with a proprietary firmware called AirOS. Any extender node with version 5.6 of AirOS and above needs to be downgraded to a 5.5.XX version of AirOS version before you can flash it with OpenWRT. | ||
| Line 10: | Line 10: | ||
* Network Manager Method: Manual | * Network Manager Method: Manual | ||
* IP Address: 192.168.1.10 (some devices will only accept from this IP) | ** IP Address: 192.168.1.10 (some devices will only accept from this IP) | ||
* Subnet Mask: 255.255.255.0 | ** Subnet Mask: 255.255.255.0 | ||
* Gateway: 0.0.0.0 (Or leave blank) | ** Gateway: 0.0.0.0 (Or leave blank) | ||
You can also use the commands: | You can also use the commands: | ||
| Line 32: | Line 32: | ||
* Log in using the credentials | * Log in using the credentials | ||
** username: ubnt | |||
** password: ubnt | |||
* Look at the Firmware information, it may say something like XM.v5.6.6.bin or XW.v5.6.6, based on this download the correct version of AirOS v5.5.10 | * Look at the Firmware information, it may say something like XM.v5.6.6.bin or XW.v5.6.6, based on this download the correct version of AirOS v5.5.10 | ||
| Line 120: | Line 120: | ||
* Reconfigure your machine with the following static network configuration. | * Reconfigure your machine with the following static network configuration. | ||
** IP address: 172.22.0.10 | |||
* IP address: 172.22.0.10 | ** Subnet mask: 255.255.255.0 | ||
* Subnet mask: 255.255.255.0 | ** Gateway: 0.0.0.0 | ||
* Gateway: 0.0.0.0 | |||
Or use the commands | Or use the commands | ||
| Line 143: | Line 142: | ||
Once configured with our firmware, an extender node will not start broadcasting an SSID until it is plugged into a home node because it must first get a mesh IP address. | Once configured with our firmware, an extender node will not start broadcasting an SSID until it is plugged into a home node because it must first get a mesh IP address. | ||
If you have a mynet n600 or n750, you can get a mesh IP for your extender node by plugging the LAN cable that was plugged into your computer into to port one or two on the back of the home node. | |||
The mesh IP that the extender node receives is the IP of the home node plus one or two. For example, if your home node broadcasts the SSID "peoplesopen.net 65.21.65" corresponding to the IP 100.65.21.65, then your extender node will receive either an IP or either 100.65.21.66 or 100.65.21.67. Once plugged into this home node, the extender node should broadcast the SSID "peoplesopen.net 65.21.66" or ".67" as well as the ad-hoc network, "pplsopen.net-node2-node" (you may not see these if your computer's WiFi antenna is only 2.4 GHz) | |||
== Testing and Network Detection == | |||
If you flashed your extender node with a dev-build of the firmware, you should now be able to ssh into to it. | |||
It is probably easiest to first ssh in to your home node over the private interface and then into the extender node with its mesh IP. | |||
First, you should immediately change or disable the root password and instead add your ssh key to `/etc/dropbear/authorized_key` (this method of login will not work when sshing through a home node) | |||
passwd | |||
Once ssh'ed into the extender node, there are few files you can play around with, | |||
`/etc/config/wireless` sets the names of the SSIDs broadcast by the antenna, you may want to change the name of the ad-hoc interface so as to distinguish it from home node's ad-hoc network | |||
Trying changing it to something like "popplesopen.net-nod2nod", then reboot the extender node and check if you can see the new name in your network list. | |||
YNext, you my be curious what you can see with your antenna, to scan for other visible networks, ssh in to the extender node and run the following, | |||
iw dev mesh0 scan | grep SSID: | |||
This should return a lengthy list of SSID, if you can see another "pplsopen.net-node2node" SSID, you should be meshing with it automatically. | |||
If you'd like to view more info about the network you can see, you can pipe the output of the previous command to a log file like so, | |||
iw dev mesh0 scan > scan log | |||
Once you are done meshing around with your extender node make sure to reset the root password with passwd or reflash the router with the standard build of our firmware. | |||
Log into your home node via SSH, and tail <tt>/var/log/messages</tt> | Log into your home node via SSH, and tail <tt>/var/log/messages</tt> | ||
| Line 164: | Line 184: | ||
There should be a debug message in the log from notdhcpserver concerning the extender node. | There should be a debug message in the log from notdhcpserver concerning the extender node. | ||
== Troubleshooting == | == Troubleshooting == | ||
=== USB to Serial Connection === | === USB to Serial Connection === | ||
If you experience trouble flashing your device via the web interface, or via the TFTP image upload method, you'll want to establish a serial connection to troubleshoot further. Methods for flashing your device involving a serial connection may become more common as devices adopt configurations to lock down [http://www.networkworld.com/article/3038722/mobile-wireless/manufacturers-start-to-lock-down-wi-fi-router-firmware-thanks-fcc.html wi-fi router firmware] to prevent flashing. | If you experience trouble flashing your device via the web interface, or via the TFTP image upload method, you'll want to establish a serial connection to troubleshoot further. Methods for flashing your device involving a serial connection may become more common as devices adopt configurations to lock down [http://www.networkworld.com/article/3038722/mobile-wireless/manufacturers-start-to-lock-down-wi-fi-router-firmware-thanks-fcc.html wi-fi router firmware] to prevent flashing. | ||
| Line 526: | Line 546: | ||
root@sudomesh-node:/# | root@sudomesh-node:/# | ||
Latest revision as of 22:57, 2 March 2018
After following the Mesh/WalkThrough, you are probably just an isolated node on the virtual People's Open Network. If you want to become part of the physical mesh, you are going to need to extend the signal from home node using what we call an extender node. An extender node is just a roof-mounted, directional antenna used to make point-to-point connections between two locations that have line-of-sight (LOS) to one another. Preparing an extender node generally consists to two stages, downgrading the proprietary AirOS firmware and flashing it with our custom build of OpenWrt.
Downgrading to older AirOS
Typically, we use Ubiquiti equipment for our extender nodes. These come with a proprietary firmware called AirOS. Any extender node with version 5.6 of AirOS and above needs to be downgraded to a 5.5.XX version of AirOS version before you can flash it with OpenWRT.
First check what version of AirOS your extender node is running, to do this,
- Edit your network settings to reflect the following:
- Network Manager Method: Manual
- IP Address: 192.168.1.10 (some devices will only accept from this IP)
- Subnet Mask: 255.255.255.0
- Gateway: 0.0.0.0 (Or leave blank)
You can also use the commands:
sudo ip link set <eth_interface> down sudo ip addr add 192.168.1.10/24 dev <eth_interface> sudo ip link set <eth_interface> up
where <eth_interface> is the name of your ethernet interface found using `ip addr` (common names include eth0, enp3s0, ...)
- Plug one Ethernet cable into your laptop on one end and into the "LAN" port of the Power-over-Ethernet (PoE) power supply on the other end.
- Plug another Ethernet cable into your extender node on one end and into the "POE" port of the PoE power supply on the other end.
- Power on the extender node by plugging in the PoE and wait for it to boot (may take a few minutes).
- Make sure you aren't connected to a wifi network that has an 192.168.1.x IP range. Disconnect/disable your wifi if necessary.
- In a browser, go to the AirOS web interface at http://192.168.1.20
- Log in using the credentials
- username: ubnt
- password: ubnt
- Look at the Firmware information, it may say something like XM.v5.6.6.bin or XW.v5.6.6, based on this download the correct version of AirOS v5.5.10
| Version | Firmware Image |
|---|---|
| XW v5.5.10 | http://dl.ubnt.com/firmwares/XW-fw/v5.5.10/XW.v5.5.10-u2.28005.150723.1358.bin |
| XM v5.5.10 | http://dl.ubnt.com/firmwares/XN-fw/v5.5.11/XM.v5.5.11.28002.150723.1344.bin |
| TI v5.5.11 | http://dl.ubnt.com/firmwares/XN-fw/v5.5.11/TI.v5.5.11.28002.150723.1518.bin |
- Back in the web interface, go to the "System" tab.
- Click the "Browse" button next to the "Upload Firmware" box
- Select the firmware image you just downloaded
- Click "Upload".
- After uploading you will be asked if you want to upgrade/install the firmware. Click yes/accept.
- Ignore any warnings about changing the default admin password, we're gonna overwrite it anyway
- Let the router finish flashing and wait for it to fully reboot.
- After it reboots, you may wanna go back into the web interface to make sure the downgrade was successful before proceeding.
XM.v6.0.4 (v6.0.4) firmware version does not appear to be downgradable via the preceding method. Instead you will need to use command-line method as follows,
ssh-keygen -f "/home/yourusername/.ssh/known_hosts" -R 192.168.1.20 scp <firmware_image.bin> ubnt@192.168.1.20:/tmp/fwupdate.bin ssh ubnt@192.168.1.20 # password is "ubnt" /sbin/fwupdate -m
Flash the Extender Node
Now that you have successfully downgraded the AirOS firmware, we can go ahead with flashing it with our custom build of OpenWRT. Start by downloading our firmware image for your model of extender node,
The extender nodes that we currently support are:
| Name | Notes | OpenWRT Doc | Firmware Image |
|---|---|---|---|
| Ubiquiti Nanostation M2 and M5 | Newer models need AirOS downgrade before flashing! Note that this will almost certainly require a USB to Serial connection (see below). | OpenWRT Docs | firmware: pre 2015 M5 versions and all M2 versions or 2015-2016 M5 versions |
| Ubiquiti Picostation 2 | Not being built in current firmware release, Previous generation 802.11g (not the same as M2) | OpenWRT Docs | firmware image |
| Ubiquiti Picostation M2 | OpenWRT Docs | firmware image | |
| Ubiquiti Nanobeam M2 and M5 | NBE‑M2‑13 and NBE‑M5‑16 work but some (earlier?) NBE‑M5‑19 have ethernet port issues. Newer models need AirOS downgrade before flashing! | OpenWRT Docs | firmware image |
| Ubiquiti Nanobridge M2 and M5 | Same as pre-2015 Nanostation M | firmware image | |
| Ubiquiti Bullet M2 and M5 | OpenWRT Docs | firmware image |
More firmware images can be found at http://builds.sudomesh.org/builds/sudowrt/fledgling/0.2.2/ar71xx.extender-node/ Also, if you are flashing for practice or testing, you can try using the dev-builds here, http://builds.sudomesh.org/dev-builds/, NOTE: USE WITH CARE, THESE PROVIDE SSH ACCESS WITH A DEFAULT PASSWORD AND SHOULD NOT BE USED FOR DEPLOYMENT NODES
- Configure your wired ethernet interface as instructed in the previous sections
- Plug one Ethernet cable into your laptop on one end and into the "LAN" port of the Power-over-Ethernet (PoE) power supply on the other end.
- Plug another Ethernet cable into your extender node on one end and into the "POE" port of the PoE power supply on the other end.
- Push a pin into the reset hole and hold it.
- With the pin held down, plug in the power to the extender node, either by plugging in it's ethernet cable or by powering on the PoE.
- Continue holding down the pin, watch the lights on the antenna - they will all flash together a few times and then flash back-and-forth in what is affectionately known as cha-cha mode (or more accurately, TFTP mode).
- Once the lights on the antenna are flashing up and down, you can let go of the pin.
- You should be able to ping the extender at 192.168.1.20.
$ ping 192.168.1.20 PING 192.168.1.20 (192.168.1.20) 56(84) bytes of data. 64 bytes from 192.168.1.20: icmp_seq=1 ttl=64 time=1.54 ms 64 bytes from 192.168.1.20: icmp_seq=2 ttl=64 time=0.826 ms
- Open a terminal (Linux or Mac?) and run the following:
git clone https://github.com/sudomesh/ubi-flasher cd ubi-flasher npm install ./flasher.js '<path to firmware>'
- The terminal should return the following,
The firmware has been successfully sent to the router. In a few seconds, the router should begin flashing its four status LEDs sweeping from left to right, then right to left (or up down, down up). This means that the router is flashing itself with the new firmware. Once the router goes back to having only the power LED lit, the router has been successfully flashed."
- Wait until the antenna has only the power LED lit and you're done.
- Reconfigure your machine with the following static network configuration.
- IP address: 172.22.0.10
- Subnet mask: 255.255.255.0
- Gateway: 0.0.0.0
Or use the commands
sudo ip link set <eth_interface> down sudo ip addr add 172.22.0.10/24 dev <eth_interface> sudo ip link set <eth_interface> up
where <eth_interface> is the name of your ethernet interface found using `ip addr` (common names include eth0, enp3s0, ...)
See Network Configuration Guides: Linux Mac
If you ping the extender node on 172.22.0.2 and it responds, it should be ready to connect to your home node on the appropriate wired Ethernet port.
$ ping 172.22.0.2 PING 172.22.0.2 (172.22.0.2) 56(84) bytes of data. 64 bytes from 172.22.0.2: icmp_seq=1 ttl=64 time=0.617 ms 64 bytes from 172.22.0.2: icmp_seq=2 ttl=64 time=0.316 ms 64 bytes from 172.22.0.2: icmp_seq=3 ttl=64 time=0.398 ms
Once configured with our firmware, an extender node will not start broadcasting an SSID until it is plugged into a home node because it must first get a mesh IP address. If you have a mynet n600 or n750, you can get a mesh IP for your extender node by plugging the LAN cable that was plugged into your computer into to port one or two on the back of the home node. The mesh IP that the extender node receives is the IP of the home node plus one or two. For example, if your home node broadcasts the SSID "peoplesopen.net 65.21.65" corresponding to the IP 100.65.21.65, then your extender node will receive either an IP or either 100.65.21.66 or 100.65.21.67. Once plugged into this home node, the extender node should broadcast the SSID "peoplesopen.net 65.21.66" or ".67" as well as the ad-hoc network, "pplsopen.net-node2-node" (you may not see these if your computer's WiFi antenna is only 2.4 GHz)
Testing and Network Detection
If you flashed your extender node with a dev-build of the firmware, you should now be able to ssh into to it. It is probably easiest to first ssh in to your home node over the private interface and then into the extender node with its mesh IP.
First, you should immediately change or disable the root password and instead add your ssh key to `/etc/dropbear/authorized_key` (this method of login will not work when sshing through a home node)
passwd
Once ssh'ed into the extender node, there are few files you can play around with, `/etc/config/wireless` sets the names of the SSIDs broadcast by the antenna, you may want to change the name of the ad-hoc interface so as to distinguish it from home node's ad-hoc network Trying changing it to something like "popplesopen.net-nod2nod", then reboot the extender node and check if you can see the new name in your network list.
YNext, you my be curious what you can see with your antenna, to scan for other visible networks, ssh in to the extender node and run the following,
iw dev mesh0 scan | grep SSID:
This should return a lengthy list of SSID, if you can see another "pplsopen.net-node2node" SSID, you should be meshing with it automatically.
If you'd like to view more info about the network you can see, you can pipe the output of the previous command to a log file like so,
iw dev mesh0 scan > scan log
Once you are done meshing around with your extender node make sure to reset the root password with passwd or reflash the router with the standard build of our firmware.
Log into your home node via SSH, and tail /var/log/messages
Sun May 8 00:51:08 2016 daemon.debug notdhcpserver: eth0.3: Physical disconnect detected Sun May 8 00:51:08 2016 daemon.debug notdhcpserver: Listening on interface eth0.3: Sun May 8 00:51:08 2016 daemon.debug notdhcpserver: client IP: 100.64.37.3 Sun May 8 00:51:08 2016 daemon.debug notdhcpserver: client netmask 26 Sun May 8 00:51:12 2016 daemon.debug notdhcpserver: eth0.3: Recieved HEARTBEAT for interface that hadn't been ACKed. ... Sun May 8 00:54:00 2016 daemon.debug notdhcpserver: eth0.3: Recieved HEARTBEAT for interface that hadn't been ACKed. Sun May 8 00:54:00 2016 daemon.info hostapd: priv5: STA 80:e6:50:0e:fe:6e WPA: group key handshake completed (RSN) Sun May 8 00:54:04 2016 daemon.debug notdhcpserver: eth0.2: Received lease request Sun May 8 00:54:04 2016 daemon.debug notdhcpserver: eth0.3: sending response (with ssl certificate) Sun May 8 00:54:32 2016 daemon.debug notdhcpserver: eth0.3: Received ACK Sun May 8 00:54:32 2016 daemon.debug notdhcpserver: eth0.3: Running up hook script Sun May 8 00:54:32 2016 daemon.debug notdhcpserver: eth0.3: Received redundant ACK Sun May 8 00:54:32 2016 daemon.debug notdhcpserver: eth0.3: Received redundant ACK
There should be a debug message in the log from notdhcpserver concerning the extender node.
Troubleshooting
USB to Serial Connection
If you experience trouble flashing your device via the web interface, or via the TFTP image upload method, you'll want to establish a serial connection to troubleshoot further. Methods for flashing your device involving a serial connection may become more common as devices adopt configurations to lock down wi-fi router firmware to prevent flashing.
The following notes describe steps to interface with a Nanostation M5 (NSM5) via the serial interface.
Order a USB to Serial Converter
USB to serial converter devices exist at a cost of $4 - $8 online, with much lower pricing and longer delivery times if ordered from China. Search for "USB to UART TTL", including "5 pin" in the search. Make sure the specifications do not mention anything other than 3.3 volts.
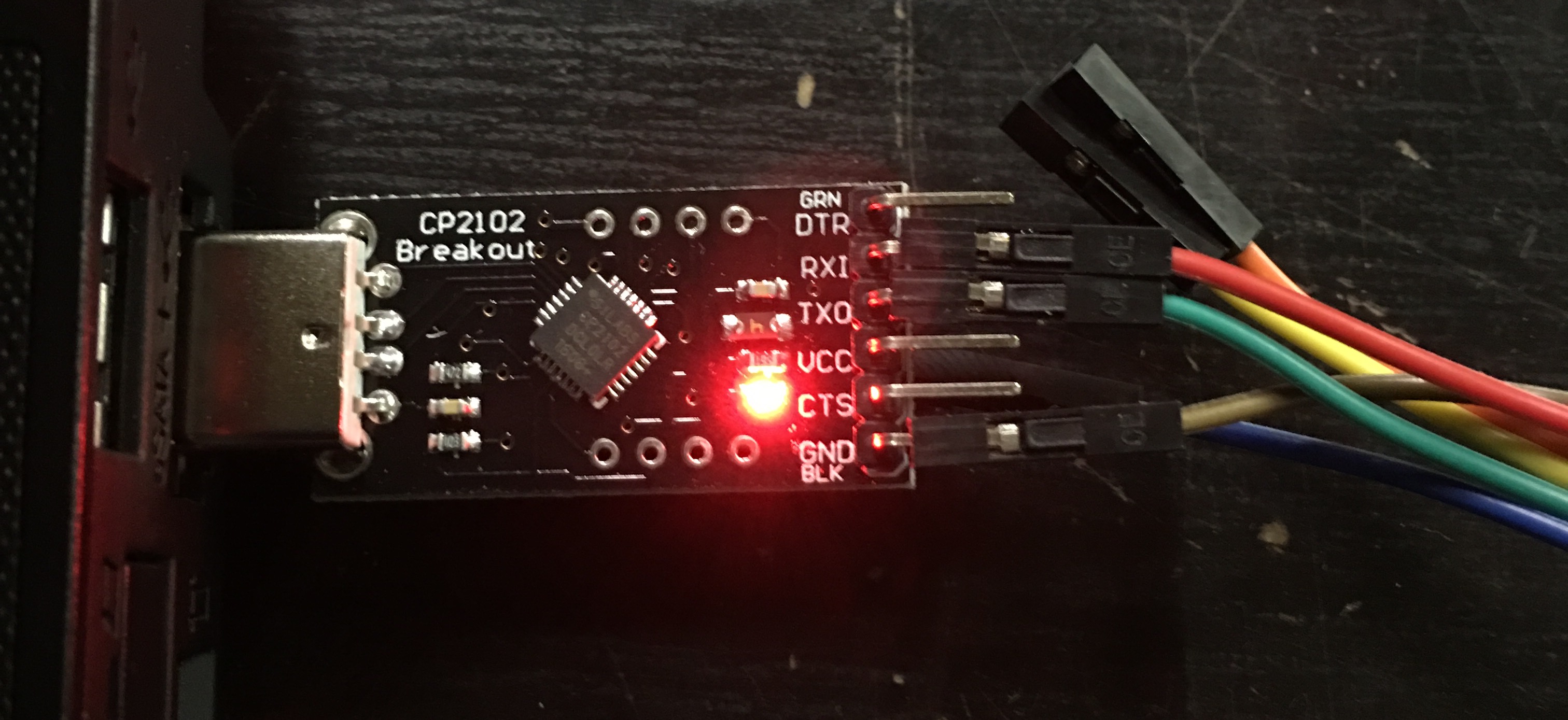
Mac OS X users may need to install a device driver for their device. For example, for devices using the CP210X chip, you can download the CP210x USB to UART Bridge VCP Driver, which is made available as /dev/tty.SLAB_USBtoUART.
Connecting to Serial
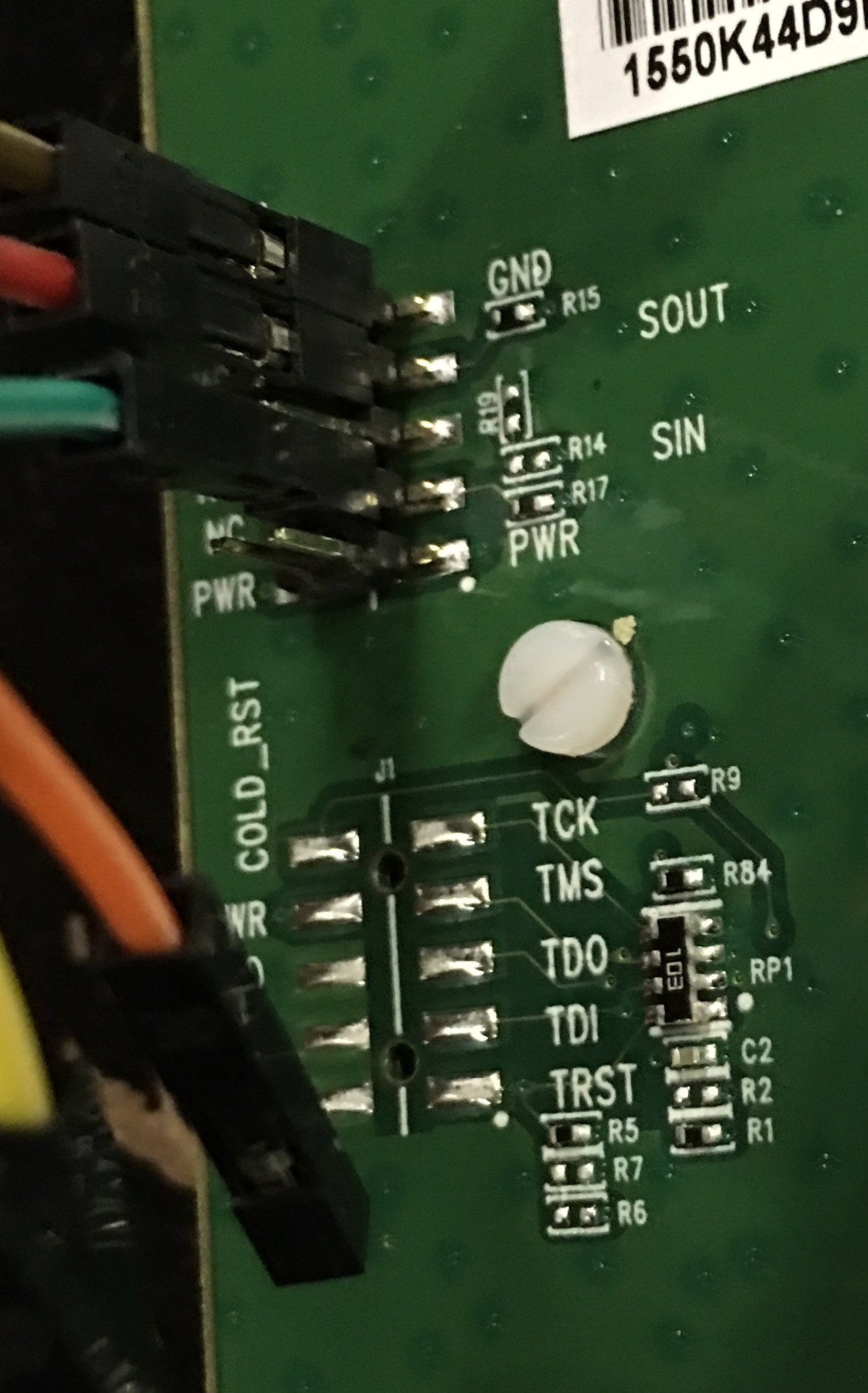
You will need to connect the following pins from the converter to the pins on the device.
- Ground (GND)
- Serial Out (Transmit / TX)
- Serial In (Receive / RX)
Begin by connecting the Ground of the converter to the Ground of the device. Next connect the Transmit/TX of the converter to the Receive/RX of the device, then connect the Receive/RX of the converter to the Transmit/TX of the device.
Nanostation M5 (NSM5) Example:
Serial Communications Program
You need to install a serial communication program. Linux users can use Minicom.
sudo apt-get install minicom
Mac OS X users can as well
brew install minicom
By default the Minicom program will attempt to use /dev/tty8, and will also attempt to initialize the device (expecting a modem) by default.
$ minicom minicom: cannot open /dev/tty8: Permission denied
Run the program so that it starts the program on the USB converter that is connected by adding -D /dev/ttyUSB0, and specify that it should skip initialization by adding -o. Mac users may need to reference a different device (such as /dev/tty.SLAB_USBtoUART).
You can also specify from the command line that it use the baud rate and '8N1' settings specified below by including -b 115200 -8.
sudo minicom -D /dev/ttyUSB0 -o -b 115200 -8
In Minicom, CTRL-A to get settings, then Press O, to access settings. Mac users will need to discover the proper META key to use with their Terminal program. iTerm uses the 'ESC' key.
Go to Serial Port Setup, use these settings:
- Set the serial device (should be /dev/tty/USB0)
- Baud Rate (Bits Per Second): 115200
- Settings '8N1' (short hand for 8 bits, no parity, 1 stop bit)
- Turn off hardware and software flow control
Reboot the device, and it will let you drop into a command line. You will then have to figure out how to enable the network from the boot loader (Uboot or Redboot) and transfer the firmware to the device to flash it.
Interupting Boot
The device will not detect the key you press unless Minicom is configured properly.
- To access the Help screen, Press CTRL-A, then press Z.
- To access the configuration/settings, press CTRL-A, then press O.
From the configuration window, select to view the 'Serial port setup'
$ sudo minicom -D /dev/ttyUSB0 -o -b 115200 -8
Welcome to minicom 2.7
OPTIONS: I18n
Compiled on Jan 1 2014, 17:13:19.
Port /dev/ttyUSB0, 21:47:56
Press CTRL-A Z for help on special keys
+-----[configuration]------+
| Filenames and paths |
| File transfer protocols |
| Serial port setup |
| Modem and dialing |
| Screen and keyboard |
| Save setup as dfl |
| Save setup as.. |
| Exit |
+--------------------------+
+-----------------------------------------------------------------------+
| A - Serial Device : /dev/ttyUSB0 |
| B - Lockfile Location : /var/lock |
| C - Callin Program : |
| D - Callout Program : |
| E - Bps/Par/Bits : 115200 8N1 |
| F - Hardware Flow Control : Yes |
| G - Software Flow Control : No |
| |
| Change which setting? |
+-----------------------------------------------------------------------+
By default the Hardware Flow Control will be enabled. Press 'F' to disable Hardware Flow Control. Press ENTER to exit the Serial port setup window, and then select EXIT to go back to the program.
At this point plug in the Ethernet cable to the 'Main' Ethernet port, with the other end connected to the 'POE' port on the Power Over Ethernet adapter that came with the device. As the device boots up, you'll see output similar to the following.
You'll need to make sure to press a key before it boots the default image.
Picostation M2HP
Insightful post on loading FreeBSD image with help from serial communications. Could be useful with troubleshooting other models.
Nanostation M2
Firmware check failure
The following are simply notes. A solution to this issue is still pending.
Flashing the Nanostation M2 (FCC ID: SWX-M2N) using the TFTP rescue mode will result in a Firmware check failure error.
$ tftp 192.168.1.20 tftp> bin tftp> put openwrt-ar71xx-generic-om2p-squashfs-factory.bin Error code 2: Firmware check failed Sent 4609024 bytes in 12.6 seconds
You can boot up the M2 with a serial connection similar to the instructions below concerning the Nanostation M5.
Board: Ubiquiti Networks XM board (rev 1.0 e012) DRAM: 32 MB Flash: 8 MB PCIe WLAN Module found (#1). Net: eth0, eth1 Hit any key to stop autoboot: 0 ar7240> mtdparts default ar7240> urescue Setting default IP 192.168.1.20 Starting TFTP server... Using eth0 (192.168.1.20), address: 0x81000000 Waiting for connection: | Receiving file from 192.168.1.10:35456 Received 4609501 bytes Firmware check failed! (-2)
The method outlined for the Nanostation M5 below doesn't work with the M2.
Update the firmware to airOS for XM board firmware v5.6.4.
Serial Connection:
ar7240> mtdparts default ar7240> urescue Setting default IP 192.168.1.20 Starting TFTP server... Using eth0 (192.168.1.20), address: 0x81000000 Waiting for connection: \
Terminal:
$ tftp 192.168.1.20 tftp> bin tftp> put XM.v5.6.4.28924.160331.1253.bin Sent 7537129 bytes in 20.8 seconds
Serial Connection:
Receiving file from 192.168.1.10:55113
Received 7537129 bytes
Firmware Version: XM.ar7240.v5.6.4.28924.160331.1253
Setting U-Boot environment variables
Un-Protected 1 sectors
Erasing Flash.... done
Erased 1 sectors
Writing to Flash... done
Protected 1 sectors
Will not overwrite u-boot partition! Skipped.
Copying partition 'kernel' to flash memory:
erasing range 0x9F050000..0x9F14FFFF: ................ done
Erased 16 sectors
writing to address 0x9f050000, length 0x00100000 ...
Copying partition 'rootfs' to flash memory:
erasing range 0x9F150000..0x9F74FFFF: .............................................................................................e
Erased 96 sectors
writing to address 0x9f150000, length 0x00600000 ...
Firmware update complete.
Resetting...
U-Boot 1.1.4.2-s594 (Dec 5 2012 - 15:23:07)
Board: Ubiquiti Networks XM board (rev 1.0 e012)
Attempting to run the same process after performing an official firmware update doesn't resolve the issue.
Nanostation M5
Official firmware from Ubiquity Nanostation M5 (NSM5)
Firmware check failure
Flashing the Nanostation M5 (FCC ID: SWX-NSM5D) using the TFTP rescue mode will result in a Firmware check failure error.
If you attempt to flash the extender and receive a 'Firmware check failed' error, then you have a version of the NSM5 that is protected from being flashed via the default TFTP method. You will need to obtain a serial to USB interface (USB to UART TTL Module Serial Converter, 5 pin) and use it to flash the firmware.
$ ./flasher.js openwrt-ar71xx-generic-ubnt-nano-m-squashfs-factory.bin Accessing http://192.168.1.20/login.cgi Connection timed out Sending openwrt-ar71xx-generic-ubnt-nano-m-squashfs-factory.bin to 192.168.1.20 using tftp put [Error: (Server) Firmware check failed]
When connected to the NSM5 via a serial connection, a similar error is displayed when attempting to load the SudoWRT firmware image.
Setting default IP 192.168.1.20 Starting TFTP server... Using eth0 (192.168.1.20), address: 0x81000000 Will reset device configuration (Reset button active after 10 seconds). Erasing sector 123..126 First 0x7b last 0x7e sector size 0x10000 .... done Waiting for connection: \ Receiving file from 192.168.1.10:49763 Received 4325788 bytes Firmware check failed! (1)
Drop into U-Boot Command Prompt
Connect a USB to Serial adapter to the correct pins of the NSM5, as shown above. Unplug the Ethernet cable from the device, and then plug it back in to provide Power Over Ethernet once again, resulting in a reboot of the device.
During the boot process, press a key to during the boot process to make the U-Boot bootloader to drop into a command line prompt.
U-Boot 1.1.4-s958 (Jun 10 2015 - 10:56:20) DRAM: 64 MB Flash: 8 MB (0xc2, 0x20, 0x17) Net: AR8236 eth0, eth1 Board: Ubiquiti Networks AR9342 board (e855-22585.1122.0030) Radio: 0777:e855 Reset: Normal Hit any key to stop autoboot: 0 ar7240>
Running TFTPd
Although U-Boot can support two protocols for transfering files, kermit or y-modem, the bootloader does not support the loadb or loady. Minicom only supports y-modem protocol.
We do not have to resort to a direct serial file transfer however. The 'mtdparts' command that is used to define flash memory partitions can be used to reset the partition table to the defaults before running 'urescue' to start the TFTP server.
ar7240> help mtdparts
mtdparts
- list partition table
mtdparts delall
- delete all partitions
mtdparts del part-id
- delete partition (e.g. part-id = nand0,1)
mtdparts add <mtd-dev> <size>[@<offset>] [<name>] [ro]
- add partition
mtdparts default
- reset partition table to defaults
ar7240> mtdparts default
ar7240> urescue
Setting default IP 192.168.1.20
Starting TFTP server...
Using eth0 (192.168.1.20), address: 0x81000000
Waiting for connection: \
In your other terminal window, run the ubi-flasher script.
$ ./flasher.js /home/redconfetti/Projects/mesh/openwrt-images/nanostation-m5/2015-2016/openwrt-ar71xx-generic-ubnt-nano-m-xw-squashfs-factory.bin Accessing http://192.168.1.20/login.cgi Connection timed out Sending /home/redconfetti/Projects/mesh/openwrt-images/nanostation-m5/2015-2016/openwrt-ar71xx-generic-ubnt-nano-m-xw-squashfs-factory.bin to 192.168.1.20 using tftp put Firmware flashing begun! The firmware has been successfully sent to the router. In a few seconds, the router should begin flashing its four status LEDs sweeping from left to right, then right to left (or up down, down up). This means that the router is flashing itself with the new firmware. Once the router goes back to having only the power LED lit, the router has been successfully flashed.
In the terminal running Minicom you should see the firmware successfully flashing.
Receiving file from 192.168.1.10:52289
Received 4325788 bytes
Firmware Version: XW.ar934x.v6.0.0-OpenWrt-r47662
Setting U-Boot environment variables
Un-Protected 1 sectors
Erasing Flash.... done
Erased 1 sectors
Writing to Flash... write addr: 9f040000
done
Protected 1 sectors
Copying partition 'kernel' to flash memory:
First 0x5 last 0x14 sector size 0x10000
................ done
write addr: 9f050000
Copying partition 'rootfs' to flash memory:
First 0x15 last 0x6e sector size 0x10000
.......................................................................................... done
write addr: 9f150000
Firmware update complete.
Resetting...
U-Boot 1.1.4-s958 (Jun 10 2015 - 10:56:20)
DRAM: 64 MB
Flash: 8 MB (0xc2, 0x20, 0x17)
Net: AR8236
eth0, eth1
Board: Ubiquiti Networks AR9342 board (e855-22585.1122.0030)
Radio: 0777:e855
Reset: Normal
Hit any key to stop autoboot: 0
## Booting image at 9f050000 ...
Image Name: MIPS OpenWrt Linux-3.18.23
Created: 2015-12-01 0:03:51 UTC
Image Type: MIPS Linux Kernel Image (lzma compressed)
Data Size: 1135619 Bytes = 1.1 MB
Load Address: 80060000
Entry Point: 80060000
Verifying Checksum at 0x9f050040 ...OK
Uncompressing Kernel Image ... OK
Starting kernel ...
[ 0.000000] Linux version 3.18.23 (sudowrt-builder@build-test2) (gcc version 4.8.3 (OpenWrt/Linaro GCC 4.8-2014.04 r47662) ) #2 Mon Nov 5
After it reboots if you see the first line mention 'sudowrt-builder', the device is booting the SudoWRT firmware build.
You can press ENTER once it is finished, and it should drop into the command line for the SudoWRT system.
[ 25.650000] jffs2: Newly-erased block contained word 0xdeadc0de at offset 0x00000000
[ 25.660000] done.
[ 25.660000] jffs2: notice: (993) jffs2_build_xattr_subsystem: complete building xattr subsystem, 0 of xdatum (0 unchecked, 0 orphan) and.
BusyBox v1.23.2 (2015-11-30 18:48:50 EST) built-in shell (ash)
._______.___ ._______.______ ._____ .___ .___ .______ ._____
:_ ____/| | : .____/:_ _ \ :_ ___\ | | : __|: \ :_ ___\
| _/ | | | : _/\ | | || |___| | | : || || |___
| | | |/\ | / \| . | || / || |/\ | || | || / |
|_. | | / \|_.: __/|. ____/ |. __ || / \| ||___| ||. __ |
:/ |______/ :/ :/ :/ |. ||______/|___| |___| :/ |. |
: : : :/ : :/
: :
-------------------------------------------------------------------------
sudo mesh v0.2 (fledgling.extender)
based on OpenWRT 15.05 (Chaos Calmer)
-------------------------------------------------------------------------
"When your rage is choking you, it is best to say nothing."
- Octavia E. Butler, Fledgling
-------------------------------------------------------------------------
root@sudomesh-node:/#