Mesh/Technical Overview
Note: You can also read the non-technical explanation of home nodes and extender nodes.
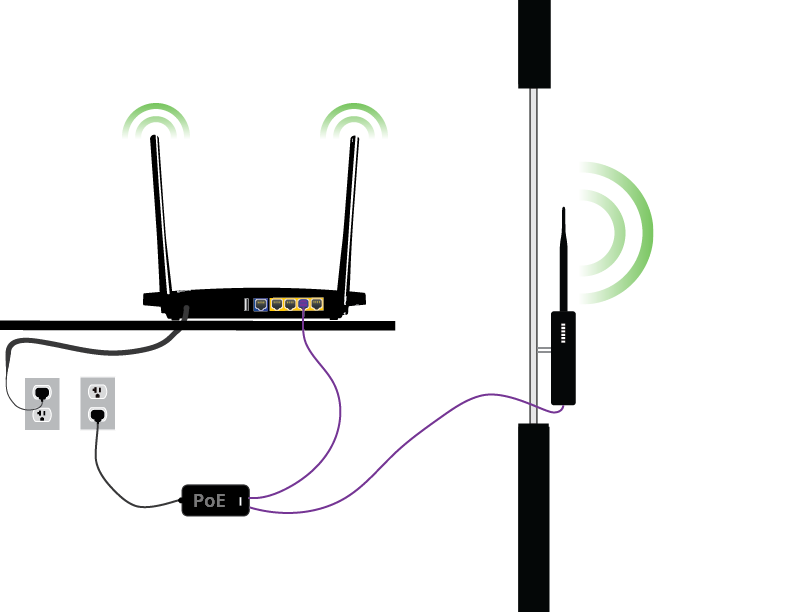
Home and extender nodes
Our mesh has two types of nodes: Home nodes and extender nodes.
The home nodes run the full sudowrt firmware and on its own a bunch of home nodes will make up a fine mesh network. The home node is a normal five-ethernet-port indoor wifi router. An extender node runs a minimal firmware and does nothing on its own. Instead, the extender node basically acts as extra radios when plugged in to a home node. The node operator can put a home node in e.g. their living room and if they later decide they want a high speed directional link to a neighbour then they can put e.g. a Nanobridge M5 running the extender node firmware on their roof and connect it via ethernet to the home node. Or they could put a Nanostation M2 pointed out their window and extend the signal further out into the street or to nearby neighbours. Each extender node extends all three networks (explained in the next section).
For home nodes we are currently only officially supporting the TP-Link TL-WDR3600. We are not planning to support anything else for the time being, though if you have a good reason please let us know. For extender nodes we are currently supporting the Ubiquiti Nanobridge M series and the Ubiquiti Nanostation M series.
The mesh is made up mostly of wifi routers using Atheros chipsets and running our own firmware based on OpenWRT, Babel and wlan slovenja's tunneldigger.
Node-owners can choose to connect the nodes to their existing internet connection using ethernet. If they have Internet access, they can share a portion of it with the mesh. The amount of bandwidth shared is limited with 'tc'. It is chosen at node-configuration time and can be changed using the simple built-in web admin interface.
The three wifi networks and IP assignment
The nodes each run three wifi networks (three SSIDs on the same physical wifi interfaces):
- The Open network with SSID peoplesopen.net is an open access point. Most people will use the network by connecting to this.
- The Mesh network with SSID pplsopen.net-node2node is an ad-hoc network that the nodes use to mesh with each other using Babel
- A private wifi network that is named by the node owner (or a name is generated) and uses WPA2-PSK.
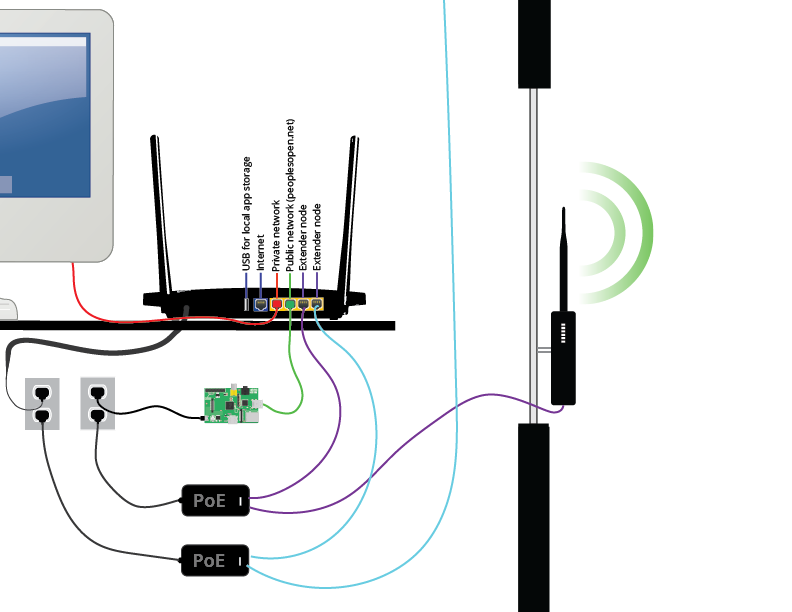
All three of these networks are available on both 2.4 and 5 GHz on the home node. They are also all three available on any extender nodes plugged in to the home node. The three different networks are extended over a single ethernet cable using VLANs.
If a node-owner is sharing internet, then the node will create a layer 2 (L2TP) tunnel to a VPN server on the Internet using tunneldigger. Babel (the mesh routing protocol) will connect over this tunnel to other nodes on the mesh, so the mesh can route traffic over the internet if no wifi path to another node is available (e.g. other nodes are physically too far away). When people connect to the peoplesopen.net access point and try to access the Internet, the traffic will flow through the VPuN, and the source IP of requests will appear to be the VPuN with the sudo mesh organization listed as the abuse contact.
The nodes run DHCP servers and each have a /24 IPv4 subnet in the 100.64.0.0/10 range that is statically assigned by coordination between mesh groups and individuals hosting and administrating their own nodes on People's Open Network (currently only the sudo mesh organization).
The private network does not limit bandwidth and provides access to both direct access to the Internet (if the node owner has hooked the node up to the Internet) and access to the mesh. Each node's private network runs on 172.30.0.0/16 and uses NAT between the private network and the mesh. It does not accept any new incoming connections from the mesh onto the 172.30.0.0/16 subnet.
Accessing Home Node via SSH
Your home node is accessible via the Dropbear Secure Shell (SSH) server on port 22.
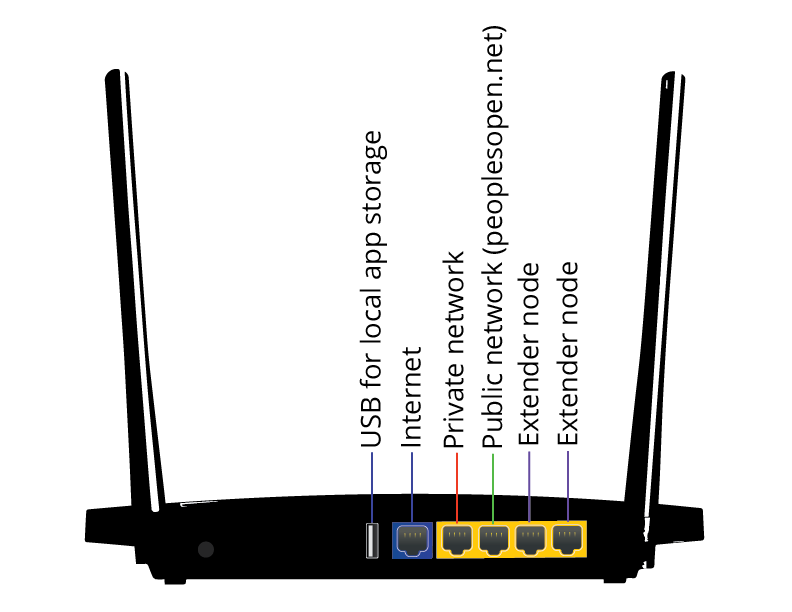
The 4 Ethernet ports that are provided with your router should be configured as follows:
- Private network with DHCP of 172.30.0.x network addresses
- Public network with DHCP of 100.64.x.x network addresses (SudoMesh network)
- NotDHCP for Extender 1
- NotDHCP for Extender 2
This may not apply to your router. For instance, the TP-Link N750 uses the opposite port assignment, with port 3 for private network, and port 4 for public SudoMesh/PeoplesOpen.net network.
Network Settings
Default Build Configuration
The IP address of your home node is 172.22.0.1 prior to configuration via the makenode utility. You can SSH into the node as root using the password 'meshtheplanet' after setting up your computer to use an IP on the 172.22.0.0/16 network.
Post Makenode Configuration
The private network configuration uses a 172.30.0.0/16 network with DHCP available for connected clients. You can configure your workstation to use the following manual network configuration so that you can SSH into your home node.
- IP Address: 172.30.0.9 (or anything other than 172.30.0.1)
- Netmask: 255.255.255.0
- Gateway: 172.30.0.1
See Network Configuration Guides: Linux Mac
The IP of your home node on the private network is 172.30.0.1, with the root password you specified when running makenode to configure it.
ssh root@172.30.0.1 The authenticity of host '172.30.0.1 (172.30.0.1)' can't be established. RSA key fingerprint is b8:9d:4a:2f:1b:f5:e1:ae:b8:19:5b:70:92:8b:7f:34. Are you sure you want to continue connecting (yes/no)?
After accepting the key by entering 'yes' and pressing ENTER, it will ask you for the root password.
SSH Keys
If you'd like to add your ssh key to the router (instead of using a root password), add it to the configs/authorized_keys file. You'll see that there are 3 other keys there for our developers. You can remove them if you'd like, but they're currently the only way we can provide remote support. During the alpha test phase we ask that you consider whether you are able to do diagnostics/debugging yourself before you remove them.
Node flashing and configuration
One of our medium-term goals is to be able to sell nodes on our website and minimize the amount of work required to re-flash/configure the nodes and provide documentation for the user. To facilitate this, our current process for new nodes is:
- A new node is flashed either automatically (using e.g. ubiquiti-flasher or merakiflasher) or manually with your own tools and the sudowrt firmware.
- The node is then configured by a sudo mesh volunteer using our makenode software.
- makenode generates SSH keys, SSH root password, web admin password and private wifi password, then it configures the node, saves the info in the node database and shuts down the node.
- makenode then automatically prints a sticker containing some basic info including wifi and web admin passwords.
- The sudo mesh volunteer attaches the sticker to the nodes power supply and puts the node back in the box with a set of instructions for how to install and use the node.
- The node is shipped to the new node owner!
Node management
All nodes set up by sudo mesh automatically allow root access using an SSH key held by a few trusted sudo mesh organizers. This is to allow us to update the firmware and troubleshoot network issues. We inform node-owners of this fact and tell them how to prevent sudo mesh from accessing their nodes, but also indicate that they should be ready to manage their own node if they choose to do this.
We don't yet have a solution for node monitoring but we're expecting to use the new version of wlan slovenja's nodewatcher software.
We don't yet have an automatic update solution in place, but we are looking at the software used by Gluon. The Gluon update system is centralized but in the long term we would like to have a decentralized system that works something like this:
- Any number of node-updater servers announce themselves on the mesh and whether or not an update is available.
- The nodes run a future version of mdnssd-min as a daemon that keeps a currently list of node-updaters.
- Once every N hours +/- a random factor, if any node-updaters have updates available, all nodes connect to a randomly chosen node-updater and request an update.
- The node-updaters send the nodes an ipk file with the update and the nodes check the signature and install it if it's signed by a trusted authority.
Detailed Documentation
- Mesh/Tracking - Problems and solutions related to tracking, logging and anonymity
- Mesh/WalkThrough - Easy how-to for setting up OpenWRT & BATMAN-adv on Ubiquiti routers
- Mesh/OpenWRT - Experiences with the OpenWRT router firmware
- Mesh/Firmware - Everything related to our firmware
- Mesh/Firmware/Flash - How to install the sudowrt firmware based on openwrt with supported hardware
- Mesh/Firmware/Splash page - Splash page / Captive Portal
- Mesh/Firmware/Bandwidth shaping - QoS / Bandwidth shaping
- Mesh/Firmware/Zeroconf - Issues related to mDNS and DNS-SD
- Mesh/Firmware/MTU_issues - MTU issues
- Mesh/Firmware/Web Admin Development - Web admin development
- Mesh/Network topology - High-level explanation of the mesh network structure
- Mesh/Specs - Specs sheet on different access points
- Mesh/Frequencies - Information on different frequencies.
- Mesh/Software tools - List of useful mesh troubleshooting tools
- Mesh/Terms - Hidden Node, Fresnal zone, and other jargons
- Mesh/Power - Stuff about power usage, batteries and solar power.
- Mesh/Monitoring - notes about how to monitor systems
- Mesh/Spectrum - Different forms of spectral analysis
- Mesh/Hardware support - Officially and unofficially supported hardware / routers
- Mesh/Relay setup - Setting up a relay node
- Mesh/Exit setup - Setting up an exit node
- Mesh/Spectrum mapping - The setup we use for mapping local spectrum and wifi usage
- Mesh/Spectrum mapping/XO-1 Laptop - How to configure an XO-1 laptop for use with our spectrum mapping setup
- Mesh/Install - physical installation notes/stories
- Mesh/Diagrams - technical diagrams to support new outreach materials